Modern cyber security is an evolving and adaptive process. As malware and other digital threats are constantly changing and improving, cybersecurity efforts, processes and technologies must also improve and use layered security approaches, especially when protecting large organizations. Many organizations and cybersecurity systems or technologies are leveraging cyber kill chains to achieve their security goals.
Whether you are an individual or represent a company, you need to know what the cyber kill chain is, how it works, and the benefits of incorporating it into your cybersecurity approaches and procedures.
An explanation of the cyber kill chain
Very simply, the Cyber kill chain The model is an adaptive model and a step-by-step process that helps organizations track, understand, anticipate and stop cyber threats of all types. The term “cyber kill chain” comes from the military term “kill chain,” which refers to a series of steps or steps necessary to prepare, attack, and destroy targets.
Indeed, the cyber kill chain as a concept was originally developed by Lockheed Martin in 2011. Then and now, the cyber kill chain helps organizations map out different steps used in common cyber attacks in order to anticipate and stop them. More importantly, the cyber kill chain helps organizations determine which stages or areas of their organization they need to protect or intercept attackers most frequently.
Note that the cyber kill chain is not a methodology by which cyber security and technology teams operate. Rather, it is a hypothetical sequence of steps that cyber attackers use to achieve their goals. In theory, by better understanding the steps an attacker will use to acquire information or money, your security team will be able to stop them more effectively.
At its core, the cyber kill chain is designed to help organizations protect themselves against more sophisticated cyber attacks, including persistent threats or APTs. APTs are especially important to guard against because their creators often spend a lot of time tracking a target or planning an attack before it happens.
The role of the cyber kill chain in cyber security
The cyber kill chain can Help your organization protect itself Against all kinds of cyber threats, from Trojans to malware to ransomware to spoofing attacks to social engineering attacks and more. It does this by putting you in the mindset of a cybercriminal, such as the creator of a malware virus.
When properly leveraged and understood, the cyber kill chain will help you not only understand how a potential attacker is likely to gain entry to your system, but it will also help you understand the best or most effective security measures to implement.
For example, if you model the cyber kill chain and determine that it is likely that an attacker will attempt to enter your system via phishing messages, you may determine that the best defense is some combination of:
· Use of more sophisticated firewalls
· Educate your employees to prevent them from opening unknown emails
· Requiring employees to change their email passwords frequently
· etc
You can tailor this approach to any potential threat, such as remote access viruses, scripts, denial-of-service attacks, and more.
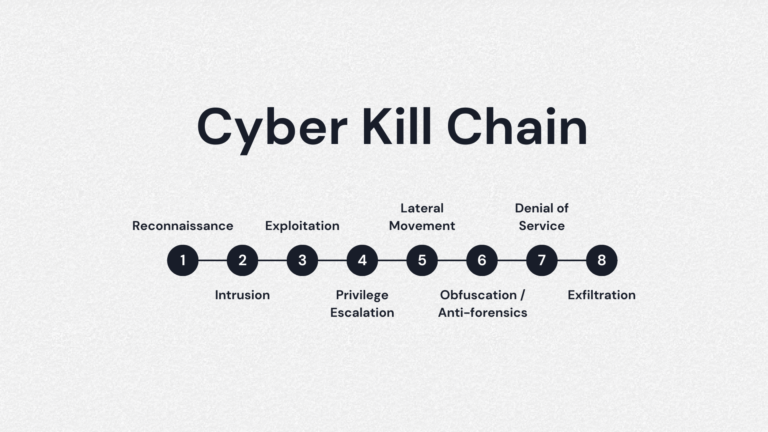
8 steps of the Cyber Kill Chain process
The cyber kill chain is complex Eight initial steps, even though Lockheed Martin’s original cyber kill chain only had seven stages. Below is a breakdown of each step one by one:
· Step 1: Tour. At this stage, the cybercriminal collects data and information about the target and prepares for the attack. For example, the attacker may collect email addresses, passwords, IP addresses, and much more. More sophisticated attackers may also scan firewalls and try to detect intrusion prevention systems, such as cybersecurity software
· Step 2: Weapon activation. At this point, the criminal creates an attack vector or path. It is basically the choice of the virus or the method by which they will gain entry into the target system. The attacker may use malware, ransomware, other virus or worm, or even a phishing program to gain access to the target system. At this point, the cybercriminal can also set up “back doors” to continue to enjoy access to the system if the original entry point is closed
· Step 3: Delivery. In the delivery phase, the cyber criminal launches his attack. For example, if they choose malware, they send a malware virus via email or other vector to gain access to the target system. At this point, the criminal may combine their chosen attack virus with social engineering techniques, such as impersonating a maintenance technician
· Step 4: Utilization. At this stage, any malicious code or virus is executed inside the target system for stealing sensitive data, escalating privileges and more
· Step 5: Installation. At this point, the attack virus, such as a malware virus or a ransomware virus, is installed on the victim’s system. This usually allows the attacker to gain control of the target’s network or system and begin operations
· Step 6: Command and Control. In the command and control phase, the attacker uses malware or other malicious code to gain control of a target device or network. The attacker may start his core targets or move laterally across the network, extending to other terminals or other computers connected to the same network in general
· Step 7: Actions on the target. In the penultimate stage, the attacker begins to carry out all his intended goals, such as destruction, data theft, infiltration, encryption and extortion
· Step 8: Monetization. This step is not part of Lockheed Martin’s original cyber kill chain. However, it is often considered an important step in modern threat analysis. At this point, the cybercriminal tries to gain income from the attack, such as demanding a ransom in Bitcoin after delivering a virus to a target network
How the cyber kill chain works
The cyber kill chain works by enabling cyber security teams or individuals to better understand the methodologies and mindset of cyber criminals. By detailing the steps above, cyber security teams or individuals can visualize how a potential cyber criminal might attack a target system.
Once they understand how a potential criminal might attack a system, they can establish defenses designed to protect the easiest or most vulnerable entry points.
How to effectively use the cyber kill chain?
Understanding the cyber kill chain is one thing. The ability to leverage and utilize it effectively is another.
Using the cyber kill chain effectively means looking at each step and applying different layers of control or security depending on what works best. Typically, those using the cyber kill chain to understand cybercriminals use six different types of security controls:
· locatingwhere the security team tries to identify or determine attempts to penetrate the system or organization
· denialwhere the security team or software stops attacks as they happen
· interferencewhere the security effort interferes with the data communication performed by the attacker to stop an attack in progress
· humiliationwhere security efforts limit the effectiveness of cyber security attacks and minimize the adverse effects
· fraudwhere the security effort misleads an attacker by providing false information or directing them to a false terminal
· brakingwhere the security efforts contain and limit the scope of the attack so that it does not cause much damage to an entire organization
Different measures may be more effective at different stages of a cyber attack.
For example, if a criminal is in the reconnaissance phase of the cyber kill chain, the best antidotes or security practices are detection and denial. The detection may be carried out by threat intelligence organizations or by leveraging a network intrusion detection system. Alternatively, security staff may practice denial; They may implement information sharing policies for all employees of the organization or use very strict firewall access control lists.
What if the criminal is at another stage in the cyber killing chain? Say they are in the delivery phase. In this case, the security team may use detection through endpoint malware protection to prevent a malware virus from being transmitted in the first place. Or they may use denial by changing management, using a proxy filter, or using a host-based intrusion prevention system.
Either way, the cyber kill chain allows cybersecurity teams to choose the best security approaches or countermeasures based on what they think is happening (or about to happen).
Advantages of Cyber Kill Chain
The cyber kill chain is very beneficial to organizations and individuals alike.
When properly leveraged, it enables cybersecurity and software teams to be more efficient, improving their value and minimizing the effectiveness of cyberattacks. Furthermore, it can result in more cost-effective security software or tools. For example, an expensive but comprehensive cyber security software suite is only effective if you use it properly. The cyber kill chain framework can help you do just that.
In addition, the cyber kill chain framework serves as an effective educational tool for beginners in cyber security issues in general. In fact, the cyber kill chain helps teach beginners how cyber security breaches occur and how cyber attacks are likely to affect an organization. Because of this, the cyber kill chain is often one of the earliest frameworks taught to new cybersecurity students or employees.
What is the difference between Cyber Kill Chain and MITER ATT&CK Framework?
Both the cyber kill chain and the MITER ATT&CK frameworks or adversary tactics, techniques, and frameworks are useful. But there are some key differences between the two approaches.
Both of these are frameworks that cyber security teams have used to understand their adversaries and anticipate cyber attacks. But while the cyber kill chain framework looks at cyber threats from a high-level perspective and has seven or eight distinct steps, the MITER ATT&CK framework combines much deeper knowledge with granular details about specific cyber attacks.
Basically, the cyber kill chain assumes that all cyber attacks follow a specific and similar sequence of attack tactics or steps in order to achieve their goals. In contrast, the MITER ATT&CK Framework is a more comprehensive knowledge base that uses environment-specific MITER ATT&CK cybersecurity information with hierarchies of tactics and techniques to enable security professionals to better anticipate and defend against specific types of attacks/viruses.
Both approaches can be beneficial for your organization, and you may want to apply both depending on the task at hand. The cyber kill chain is better for beginners as it offers simplicity and a basic understanding of cyber attack processes.
The MITER ATT&CK is a bit more comprehensive and better for experienced cyber security analysts or teams. In this way, MITER ATT&CK is much more useful for threat hunters or “red teams”, as well as anyone who plans and implements new security controls or policies, such as network architects and administrators.
to wrap
As you can see, the cyber kill chain is an important and adaptable framework that allows organizations to trace the stages of cyber attacks, identify vulnerabilities ahead of time, and assist in cyber security efforts. It’s an integral part of modern cyber security technologies and systems, so you should leverage it in your business starting today.
Technologies like PC Matic can help you perform the various steps in the cyber kill chain. For example, PC Matic Pro offers proactive security and remote management services to help you anticipate and stop cyber threats. Contact us today to learn more.